It doesn’t matter how strong the authentication is, it always comes back to three categories.
– Something you know
– Something you have
– Something you are
An example of something you know is a password for a PSK WLAN. Something you have can be the laptop that is part of the active directory or a digital certificate that can be used for EAP-TLS. The last category, something you are, is not really used in the wireless industry, but in the technology industry, for example, by unlocking your iPhone using your fingerprint. When you use two categories together we are talking about multifactor authentication.
When you decide what kind of categories you will use, for authentication to the wireless network, there are several things you need to take into consideration. If you pick a banking environment you want that not everybody can connect to the network. So, people need a password, but also the laptop needs to be known (for example in active directory). When you go to the local Starbucks you can use every device and a password is good enough and is multifactor authentication overkill and not cost efficient.
When you are authenticated, the next question is for what resources are you authorized. You don’t want to see the emails from someone else. So, there needs to be a check that you are the one that you say you are. The Remote Authentication Dial-in Users Service (RADIUS) is an example that can perform AAA in an enterprise wireless network. AAA stands for Authentication, Authorization, and Accounting. Accounting is important for your history and troubleshooting, such as who was logged in and where he had access. This is all part of the 802.1X framework.
802.1X
As you know, wireless standards are 802.11. We are talking about standard 802.1X, so this is not a wireless standard. 802.1X is a port-based access control standard that is also used in the wired network. 802.1X use Extensible Authentication Protocol (EAP) as a layer 2 authentication to make sure that the right users are authorized for the resources they want to access. There are three components in the 802.1X framework.
Supplicant: this is the end user that wants to access the resources. It is a device with some software that requests to access the network, for example a laptop or a phone. It communicates with the Authenticator Server through the Authenticator. It uses EAP to communicate at layer 2. After the authorization, it is able to communicate on layer 3-7. There are different types of EAP protocols, and the client (supplicant) and the Authentication Server (RADIUS) need to support the same EAP protocol.
Authenticator: this is a device that blocks or allows the traffic. If the user is allowed to access the resources, the port will go from a blocked (controlled) state to an unblocked (controlled) state. The uncontrolled state passes through EAP traffic and opens at the moment that the EAP communication starts. The controlled state passes through all the traffic at the moment that the 4-way handshake is finished successfully. In a WLAN with autonomous access points, the access points are the authenticator. In an environment with a WLC, the WLC is the authenticator. When you configure point-to-point connections, the root bridge is the authenticator and the non-root bridge is the supplicant. The authenticator talks with the authentication server, and the validation between those components is with a shared secret that needs to be configured on both sides. Port UDP 1812 or 1645 is for Authentication and port UDP 1813 or 1646 is for Accounting.
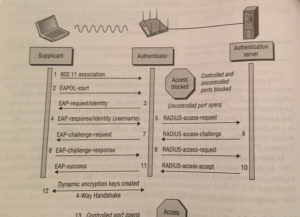
Authentication Server (AS): this is the server that validates the user and if the user is authorized for accessing the resources. An example of the AS is the RADIUS server. The RADIUS server has a database with users, but most of the time it is an external Lightweight Directory Access Protocol (LDAP) compliant database like active directory.
The authentication server is not only for authentication, throughout the years, the AS has enhanced with features like VLAN assignment. When a user is authorized and part of the student group, it will be assigned to the student VLAN. This is the same as VLAN tagging on a wired switch port or role-based access control (RBAC). Another option for AS is Network Access Control (NAC). Beside authentication, NAC can also do endpoint security like making decisions based on operating system patches and up-to-date virus scans.
As mentioned earlier, there are several ways to authenticate to an AS. The most common is the username password combination or a digital certificate. You see those certificates also when you enter HTTPS websites. The certificate can be used to verify the computer and in combination of the username and password, we are back to the multifactor authentication.
Protected Access Credentials (PAC file) is used with EAP-FAST. When you use a client certificate, you also need a Public Key Infrastructure (PKI). Because of the configuration, maintenance, and the cost of a PKI server, is is not possible for every company. Cisco designed the PAC files for authentication.
Other options are tokens (One Time Passwords). This can be a small device or an app on your mobile phone. You can also use smartcards. Al those things are examples of something you have.
