In this blog, I will describe the legacy encryption mechanisms.
Wired Equivalent Privacy (WEP)
As stated in an earlier blog, SKA should not be used as an authentication mechanism. WEP is not secure at all and should not be used anymore. WEP can be used as authentication method in SKA, but also as encryption method in SKA and OSA. WEP encrypt the MSDU payload. There are two versions of WEP, the 64-bit version or the 128-bit version, also referred to as 40-bit and 104-bit.
WEP uses Integrity Check Value (ICV) in the front of the data to prevent any modification. WEP also uses an Initialization Vector (IV). The IV is in total 24 bits, this is the reason why the 64-bit is also referred to as 40-bit. 64 bits is a 40-bit static key and a 24-bit IV. The IV is in clear text, but every new IV will be a new created IV. In total, there are 16,777,216 possibilities. Someone who use eavesdrops with wireshark, for example, and waits long enough will have all the 16,777,216 clear text IVs that are possible.
Then there is also the transmission key. This is the static key that is used for encryption and needs to be equal on the client and the access point. You can use a different key for encryption and decryption as long as the other side uses the same key. For example, access points use key #1 for decryption and key #2 for encryption. As long as the client uses key #1 for encryption and key #2 for decryption then there will be no issues.
WEP use a Cycle Redundancy Check (CRC) on the plain text data that needs to be encrypted, and WEP adds the ICV to the end of the data. Till so far, the data is clear text. WEP generate a 24-bit IV, also clear text. The IV is combined with the static key for encryption. The IV and the Key are the seed for the ARC4 algorithm that generates random bits known as the keystream. The keystream is equal in length as the plain text data. The plain text data and the keystream are using the XOR process and the end result is the WEP cipher text. Before the cipher text is the IV added as prefix, as well in clear text. So, when you use wireshark you are able to read the IV, which is a part of the encryption key. Another prefix is the number of the four-possible static keys that are used. In the below picture, you see the whole process in a scheme. The other picture describes the frame format.


Since part of this encryption method is in clear text, there are some weaknesses in WEP, and as you probably know, WEP is broken and can be hacked.
IV Collision Attack
As mentioned there are in total 16,777,216 possible IVs. If the hacker has patience it doesn’t take a lot of time to wait for all the possible IVs. Since the IVs are in clear text, it is easy to read those.
Weak Key Attack
Since the IV is part of the ARC4 algorithm, it is easy for the hacker to recover the secret key. It is like math, you know the answer and one of the variables. It is easy to figure out what the other variable must be.
Reinjection Attack
If it takes too long for all the IVs to pass in your packet capture, it is possible to reinject some data to fasten the IV generation.
Bit-Flipping Attack
With the previous attacks, you can easily recover the WEP key. With the WEP key you can decrypt all the data frames.
Temporal Key Integrity Protocol (TKIP)
The Temporal Key Integrity Protocol is an enhancement of WEP. This protocol is more secure than WEP, since WEP is broken. IEEE 802.11i first defined TKIP for a stronger encryption, but as the name said it was temporary. In 802.11i also CCMP/AES is defined, but not all the legacy devices were able to support this newest technology.
Why is TKIP better than WEP?
Temporal keys
TKIP use temporal keys between two radios. Every two radios use a 4-way handshake to create a temporal key.
Sequencing
TKIP uses a per-MPDU TKIP Sequence Counter (TSC). Every packet that is out of order will be dropped, this is a defence against the reinjection attack.
Key mixing
This is a stronger mechanism for the seed that is used for the ARC4 algorithm. The process to create a seed is in two phases.
Enhanced Data Integrity
TKIP uses stronger data integrity, known as the Message Integrity Code (MIC) or Michael. This is a defence for the Bit-Flipping attack that could be used with WEP.
TKIP Countermeasures
The countermeasures are used for hackers that still try to hack the key. If there are two invalid MICs within 60 seconds, countermeasures will be in place and will rekey the TKIP session key.
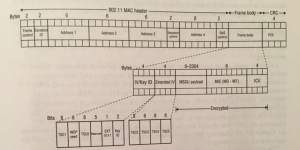
Below you will see the whole TKIP process.

First there will be a generated 128-bit temporal key. This key is generated from the 4-way handshake process. This is the Pairwise Transient Key (PTK) or the Group Temporal Key (GTK). GTK is used for broadcast and multicast, PTK for unicast traffic. After that there will be a 48-bit TKIP sequence counter (TSC) generated and separated in 6 octets (TSC0 – TSC5).
Phase 1: a mix of TSC2 – TSC5, the Transmit Address (TA) and the Temporal Key (PTK/GTK). This is the TKIP-mixed Transmit Address and Key (TTAK).
Phase 2: a mix of the TTAK, TSC0, TSC1 and the Temporal Key. This is called the WEP seed. As you can see, the WEP seed is more complex than the WEP seed in WEP. The WEP seed is used for ARC4 and to create the keystream.
For data integrity TKIP uses MIC. MIC is to defend against bit-flipping, fragmentation attacks, redirection attacks, and impersonation attacks. MIC computation is using the Destination Address (DA), Source Address (SA), MSDU priority and the plain text. The generated MIC will add at the end of the plain text.
TKIP has already methods against hackers that misuse the MIC. There is logging when there is a MIC failure. If there are two MIC failures within the 60 seconds, the client or access point disables all TKIP frames for 60 seconds. After that a new temporal key will be generated. The frames look as followed.
There are still weaknesses in TKIP, but as the name said TKIP is a temporary replacement for WEP before CCMP/AES was a standard.
