Probably you would not believe it, but there are common wireless issues/limitations as well.
Insufficient Capacity
Think about networks with mixed PHYs. When there is an HT only network and an ERP client is going to associate with this network. The access point will implement a protection mechanism that have influence on the throughput. Another limitation can be on switch level. Think about a switchport that only supports 100 Mbps. The access points nowadays need at least 1 Gbps or the uplink from the switch has not enough throughput.
Co-channel and Adjacent Channel Interference
To start with the Adjacent Channel Interference (ACI). There are two types of ACI. The first type is called overlapping ACI. Overlapping means that you use two channels that are too close to each other and overlap. For example, 1 and 2, but if you use access points with high output powers channels 1 and 3 or even channels 1 and 5 can be seen as ACI. The other type of ACI is the non-overlapping ACI. In the 2,4 GHz you have channel 1, 6, and 11 that are non-overlapping, but in cases of high output power and close to each other it is possible that you see a little bit of overlap.
Co-Channel Interference (CCI) is when two nearby access points are on the same channel. The problem with this is that the access points will accept clients from other BSSs since they are all on the same channel. A way to reduce the impact on CCI is to reduce the number of SSIDs. Management and control frames can add up some overhead. In a 2.4 GHz environment, you cannot avoid CCI. So, to reduce the overhead you need to use less SSIDs, disable some lower data rates, and limit the access point on one channel as much as possible.
Both interferences can be seen by using a protocol analyzer. For ACI look for retransmission frames. Retransmission frames occur with ACI, and as long as they are not more than 10% it is okay. For CCI the utilization per channel is important.
RF Noise and Noise Floor
You can compare this with a real situation. Standing in a room where everybody is yelling and you are trying to talk with someone. Signal strength is important, but we also refer to the Signal to Noise Ratio (SNR). The SNR is the noise floor (dBm) minus the signal strength (dBm). For example, a noise floor at -95 dBm and a signal strength at -70 dBm will be a SNR of (-95 – -70) = 25. A SNR of 20+ is good for data and a SNR of 25+ is good for voice. So below those values can be problematic. So, a good signal strength (-65 dBm), but with a noise floor at (-80 dBm) is the SNR 15 dBm. That is not even good enough for data.
RF Interference
As you could read in the blog about spectrum analysis, you know that there are multiple non-Wi-Fi sources that can interfere with the wireless signal, like microwaves. Beside that there are also wireless interferences as CCI, ACI and Noise. You can find the interference by spectrum analyzers, but as well with protocol analyzers and looking for CRC errors and retransmission frames.
Multipath
Nowadays there are PHYs that take advantages of multipath, MIMO. HT and VHT are based on MIMO, but there are still older PHYs that cannot deal with multipath. With older devices multipath have a negative effect on the signal (downfade, out-of-phase or nulling).
It is hard to find out about multipath because you don’t see the waves in the air. You need to look at retransmissions, dead spots. When you use older PHYs you want to fix multipath as much as possible. You can remove the objects that occur multipath, this can be hard if those objects are walls.
Hidden Node
Hidden Node is happening in all WLAN environments, it happens when another client cannot hear the client that is transmitting. This can be because of obstacles, near-far, modulation and distributed system. For those issues RTS/CTS need to be enabled on the client. To avoid this, you can remove the obstacle, but again that is mostly not possible, or increase the power level at the clients. Another hidden node issue is when the client hears two access points, but the access points don’t hear each other.
Near-Far problem
Near-far issues appear when the client is too far away with a low power (far) or a high-powered client close to the access point (near). To find this out you will see clients that cannot connect with the access point. To avoid this, increase the power at the client that is far or decrease the power at the client that is near. In a far problem, extra access points might help as well. Nowadays you don’t see those issues much anymore. The power at the access point are less and more access points are deployed.
Weather
Fresnel zones are important with bridge links. Snow or growing trees can interfere with the first Fresnel zone and this will reduce the quality—not only issues on the RF waves, but also misalignments of the antennas. Think about heavy snow or ice on the antenna or heavy wind.
QoS
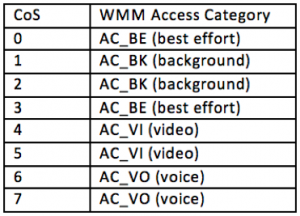
In the blog about wired issues, there was also a part about QoS, the mapping with the CoS values. Those values are also mapped to the WMM Access Category in the wireless networks. In the below table, you see the WMM mapping to CoS.
Other WLAN issues
There are also security issues that can be addressed. Clients that don’t support WPA2 cannot associate to a network that is WPA2 only, wrong PSKs or doesn’t support roaming solutions as key caching or 802.11r. In those cases, there will be a delay in roaming,
Think about weak or default passwords. On the internet are lists available with all the default passwords. If you never change those default passwords, there is a security leak.
Not updating your wireless networks, there are older software versions that has security vulnerabilities.
Rogue access points cannot only interfere your network, but also break into your network. Stay alert for those devices and scan your network often to find rogue access points.
Other ways that your wireless network can be insecure are the default SNMP community strings. The default is “public” and “private.” When you don’t change those, they are easy objects for intruders. Also, easy object is cisco discovery protocol. This protocol shows a lot of information that intruders need to know to hack the system.
