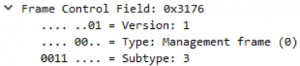
Authentication/Deauthentication Frames
To enter the authentication state (remember the different states a client can be assigned to) you need authentication frames. There are four frames during the authentication. First the client transmits an authentication frame and the access point replies with an acknowledgement and an authentication (response) frame. The client replies with an acknowledgement.
![]()
The first frame is from the client to the access point and shows which type of authentication it will use. As discussed earlier there are two types, open system authentication and shared key authentication.
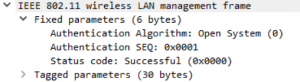
This frame uses open system authentication (0). When it uses shared key authentication, the bit is set to 1. The authentication sequence shows that this is the first frame, so from the client to the access point. (seq number is 1). Last is the status code. 0 is successful and 1 is a failure. In my situation, the code is 0.
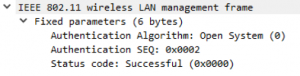
The response from the access point is almost identical to the first authentication frame. The only difference is the sequence number.
The deauthentication frames are to inform that the client is not authenticated any more. The reason can be that the client is inactive too long. In the deauthentication frame is the reason why the client is deauthenticated. In this example, the reason is unknown.
![]()
You can filter in wireshark with wlan.fc.type_subtype == 0xb (subtype 11) (authentication frames)

You can filter in wireshark with wlan.fc.type_subtype == 0xc (subtype 12) (deauthentication frames)
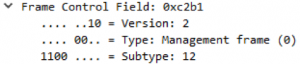
Association/Disassociation Frames
After the authentication stage, there is the association stage. In this stage, the client starts with an association request, the access point replies with an acknowledgement and an association response. The last step is an acknowledge frame from the client.
You can see in the process below that there are two association requests transmitted from the client, the second is a retransmit. Between the acknowledgement and the association response frame is a beacon frame.
![]()
There are similarities between a probe request frame and an association request frame. Both show the SSID parameters, Supported and Extended Supported Rates, Capabilities and vendor specification. There is a field that has some confusing, it is named the Listen Interval. The Listen Interval tells the access point how often it wakes up in power save mode to listen to the beacon frames. It is not sure how this affects the DTIM from the access point. For example, what if the DTIM is 5 and the Listen Interval is 3. Every 3rd beacon the client wakes up, but the DTIM that tells if there are data is every 5th beacon.
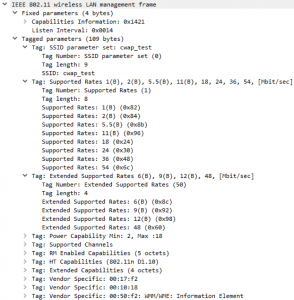
After the request the access point transmits an acknowledge and an association response. Before this, it will verify all the fields. f there is a mismatch, there will be no association with the access point. The important fields in the association response frame are the status code and the Association ID field. Beside those two you have capabilities information like the probe response and beacon and the supported rates.
There are several status codes. In this example the status code is 0 which means successful. Other codes are 12 for rejection for some reason outside the scope; 17 means that the access point reached the maximum number of clients, and 18 is that the client does not support all the data rates so it cannot associate with the access point.
Disassociation frames are to disassociate from an access point by example roaming. They are like the deauthentication frames and have a reason of disassociation. Again in this example it is unknown.

You can filter in wireshark with wlan.fc.type_subtype == 0x0 (association request frames)
You can filter in wireshark with wlan.fc.type_subtype == 0x1 (association response frames)
You can filter in wireshark with wlan.fc.type_subtype == 0xa (subtype 10) (disassociation frames)
Reassociation Request/Response Frames
Those frames are used with roaming. When a client sees a better access point it transmits a reassociation request and receives a reassociation response.
The reassociation request frame is like the association request frame. In the reassociation request frame is a field with the current access point address. The reassociation response from the access point is also like the association response.
You can filter in wireshark with wlan.fc.type_subtype == 0x2 (reassociation request frames)
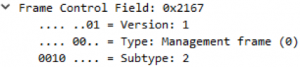
You can filter in wireshark with wlan.fc.type_subtype == 0x3 (reassociation response frames)