I am not yet studying for CWSP, but for CWAP, it is necessary to understand the frames when a client connects to an access point. If something goes wrong in the authentication/association you need to understand how to troubleshoot. Before starting with my study notes for CWSP, this is a quick overview of what is needed for CWAP to understand the states.
There are three states:
– Unauthenticated/Unassociated
– Authenticated/Unassociated
– Authenticated/Associated
State 1: Unauthenticated/Unassociated
At this point the client is not connected to any of the access points in the network. There is no communication possible in this state. There are two ways to go to the next state. The first one is passive scanning. With passive scanning, the access point initializes the process by sending beacon frames. The client receives those frames and knows where the access points are and can connect to the access point with the best signal.
The second possibility is called active scanning. This is initialized from the client. The client sends out probe requests and all the access points that receive the probe request reply with a probe response. The access point will pick the access point with the best signal.
State 2: Authenticated/Unassociated
When the client has picked the best access point, it will try to authenticate with the access point. There are two methods of authentication. The first one is Open System Authentication and the second is Shared Key Authentication. The first one is an open authentication that is not secure at all, but is still today the method that is used the most. The second is ‘more secure’.
Open System Authentication
There is no authentication at all, it is open. The client transmits an authentication frame that it wants to use Open System Authentication (OSA). The access point responds with an ACK frame. The access point responds also with a positive authentication and the client responds with an ACK frame. OSA is still used today for open networks like hotspots, but also for WPA2 personal and enterprise networks. The authentication is open, but WPA2 personal or enterprise is secure enough that it can rely on OSA.
Shared Key Authentication
Shared Key Authentication (SKA) is used with the deprecated Wired Equivalent Privacy (WEP). There are several weaknesses discovered in WEP so it is better not to use it anymore and with that also not use SKA. For authentication, the client and the access point need to use the same key to authenticate each other. The key can be cracked in a couple of minutes.
You can go back from state 2 to state 1 with a deauthentication frame. Those frames are only for advisory as an access point cannot prevent a deauthentication. The access point will respond with an ACK. In the frame is a reason code, for example reason code 3 means that the STA is leaving the BSS.
State 3: Authenticated/Associated
After the device is authenticated, the device needs to associate. A client can be authenticated to multiple access points, but only associated to one access point. There are four frames between the client and the access point. It is possible (not often) that a client successfully authenticates, but fail during the association process. The reasons are status that is shown is an association response. Some of the status numbers are 12 (rejected, because outside the scope), 17 (access point has the max number of clients), 18 (client doesn’t support the data rates).
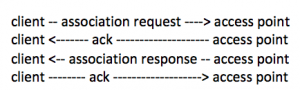
Reassociation frames occur when a client roams from one access point to another access point. A disassociation frame is like the deauthentication frame and an advisory frame cannot be denied by the access point.
